A comprehensive guide for IT leaders on implementing SASE in a 300-seat multi-region company. Learn strategies, vendor reviews, and best practices for 2026.
The modern enterprise is no longer confined to a single headquarters. For a 300-seat company operating across multiple regions—whether through remote workforces, international branch offices, or cloud-hosted applications—the traditional network perimeter has dissolved. This shift has created a critical security and performance gap that legacy infrastructure, such as MPLS and disparate security appliances, simply cannot bridge.
The solution lies in the Secure Access Service Edge (SASE), a framework that converges wide-area networking (WAN) and cloud-delivered security into a single, unified service. SASE is not just a technology upgrade; it is an architectural decision that defines how your distributed organization connects users to applications securely and efficiently for the next decade.
This detailed playbook is designed for IT decision-makers, cloud architects, and business leaders in mid-sized, multi-region companies. We will provide a clear, six-phase implementation strategy, analyze the key challenges of global deployment, and review the leading SASE vendors to help you select the right platform for your specific needs.
The Strategic Imperative: Why Multi-Region SASE is Non-Negotiable
For a company with 300 employees spread across different time zones and regulatory environments, the complexity of managing a traditional network scales disproportionately to the size of the IT team. SASE addresses this by moving the control plane to the cloud, offering a unified, policy-driven approach that is essential for global operations.
Key Challenges of the Multi-Region Mid-Market
Implementing SASE in a multi-region environment introduces specific challenges that must be addressed strategically:
- Latency and Performance Consistency: In a traditional hub-and-spoke model, traffic from a remote office in Asia might be “backhauled” to a central data center in Europe for security inspection. This introduces unacceptable latency, crippling application performance and user experience. A multi-region SASE deployment must leverage a global network of Points of Presence (PoPs) to ensure traffic is inspected and routed locally, minimizing latency for all users, regardless of location.
- Regulatory Compliance and Data Residency: Operating across regions means adhering to diverse regulations like GDPR (Europe), CCPA (California), and various national data sovereignty laws. A SASE platform must offer the flexibility to enforce granular security policies that dictate where data is processed and stored, ensuring compliance without compromising global security standards.
- Cost and Operational Overhead: Mid-market companies need to maximize ROI. Maintaining separate contracts, appliances, and skill sets for networking (SD-WAN) and security (FWaaS, SWG, ZTNA) is expensive and complex. A converged SASE solution simplifies the stack, reduces vendor sprawl, and lowers the total cost of ownership (TCO) by minimizing the need for specialized, siloed expertise.
The Multi-Region SASE Implementation Playbook: A 6-Phase Strategy
A successful SASE migration is a journey, not a switch-flip. This structured, six-phase playbook provides an actionable roadmap for your 300-seat, multi-region enterprise.
Phase 1: Discovery and Comprehensive Gap Analysis
Before touching any infrastructure, you must establish a baseline. This phase is about understanding your current state and defining the desired future state.
- Audit Application Usage: Categorize all applications (SaaS, IaaS, on-premises, legacy) and map user access patterns. Identify which applications are most sensitive to latency (e.g., VoIP, video conferencing) and which require the highest security scrutiny (e.g., ERP, HR systems).
- Map Regional Footprint: Document all physical locations, remote user concentrations, and cloud environments (AWS, Azure, GCP). Critically, assess the quality and cost of local ISP connectivity in each region.
- Define SASE Goals: Clearly articulate the business drivers. Are you prioritizing cost reduction, enhanced security posture (Zero Trust), or improved user experience (latency reduction)? These goals will inform your vendor selection.
Phase 2: Architectural Decision and Vendor Shortlisting
The SASE market is split between two fundamental architectural approaches: Proxy-Based (Security-First) and Route-Based (Network-First). Your choice here is paramount.
- Proxy-Based (SSE-First): Vendors like Zscaler and Netskope excel at security by terminating all connections at the cloud edge for deep inspection. This is ideal for cloud-heavy organizations prioritizing Zero Trust and data protection. However, it can be challenging for legacy applications.
- Route-Based (Converged): Vendors like Cato Networks and Palo Alto Networks treat traffic as a flow, maintaining traditional networking constructs (routing, subnets). This offers broader application compatibility and is often better for organizations with significant on-premises or legacy data center assets.
Based on your Phase 1 goals, shortlist 2-3 vendors that align with your chosen architecture.
Phase 3: Proof of Concept (PoC) and Regional Pilot
Do not attempt a global rollout immediately. Select a single, representative regional office or a group of 20-30 remote users for a controlled pilot.
- Test Latency and Throughput: Measure performance for mission-critical applications before and after SASE deployment. Pay close attention to the vendor’s PoP proximity to your regional sites.
- Validate Application Compatibility: Ensure all legacy and proprietary applications function correctly. This is where the architectural decision from Phase 2 is validated.
- User Acceptance Testing (UAT): Gather feedback from end-users on their daily experience. A successful SASE deployment must be invisible and non-disruptive to the end-user.
Phase 4: Policy Standardization and Governance
The core benefit of SASE is unified policy management. This phase involves translating your security and networking requirements into a single, global policy set.
- Implement Zero Trust Principles: Adopt a “never trust, always verify” model. Policies should grant access based on user identity, device posture, and application context, not network location.
- Global Policy, Local Overrides: Establish a global security baseline (e.g., malware protection, content filtering). Create specific, granular overrides only where necessary for regional compliance (e.g., blocking access to certain cloud services in specific countries to meet data residency laws).
- Integrate Identity (IdP): Integrate your SASE platform with your Identity Provider (IdP) (e.g., Okta, Azure AD) to ensure a seamless, single sign-on experience and consistent identity-based access control (ZTNA).
Phase 5: Phased Global Migration and Cutover
Execute the rollout in manageable stages, prioritizing regions based on risk or business need.
- Branch Office Migration: Begin with smaller, less complex branch offices, moving them from legacy firewalls/routers to the SASE edge device (or client).
- Remote User Migration: Use the SASE client to migrate all remote users, replacing traditional VPNs. Ensure robust training and support documentation are available.
- Decommission Legacy Hardware: Once a site is fully migrated and stable, decommission the legacy hardware to realize immediate cost savings and reduce the attack surface.
Phase 6: Continuous Optimization and ROI Realization
SASE is a cloud service, meaning optimization is continuous.
- Monitor Digital Experience: Use the SASE platform’s monitoring tools (e.g., ZDX, DEM) to proactively identify and resolve connectivity issues before users report them.
- Measure ROI: Track key metrics such as reduced latency, lower hardware/maintenance costs, and decreased security incident response times. Fortinet, for example, has reported that its integrated SD-WAN and SASE solutions can deliver over 300% ROI over three years.
- Adapt to Trends: Regularly review new features from your vendor (e.g., AI-augmented security) and adjust policies to address evolving threats and business needs.
Review of Key SASE Vendors for the Mid-Market
Selecting the right vendor is the most critical decision. For a 300-seat company, the balance between feature richness, complexity, and cost is key. Below is a comparison of the four market leaders, tailored for the mid-market perspective.
Visual 1: SASE Vendor Comparison Table (300-Seat Focus)
| Vendor | Primary Architecture | Mid-Market Focus | Key Strength | Key Consideration |
|---|---|---|---|---|
| Cato Networks | Route-Based (Converged) | Agility, Simplicity | Global Private Backbone, Ease of Deployment | Less granular control for advanced networking teams |
| Palo Alto Networks (Prisma SASE) | Route-Based (Integrated) | Security, Consistency | Unified policy with existing Palo Alto firewalls | High complexity, premium cost, intricate licensing |
| Zscaler | Proxy-Based (SSE-First) | Zero Trust, Scale | Proven security at massive scale, “darknet” architecture | Can be complex for legacy apps, support challenges for smaller clients |
| Netskope | Proxy-Based (Data-Centric) | Data Protection, CASB | Superior DLP and CASB capabilities, data context awareness | Newer ZTNA maturity, client can be resource-intensive |
Note: This table should be rendered as a comparison table visual in the final blog post.
Deep Dive: Single-Vendor vs. Best-of-Breed
For the 300-seat company, the single-vendor SASE approach (e.g., Cato Networks, Fortinet, Palo Alto) is often the most pragmatic choice.
- Single-Vendor Advantage: A single platform, single management console, and single support contract drastically reduce operational complexity and TCO. This is vital for lean IT teams who cannot afford to maintain expertise across multiple, disparate systems.
- Best-of-Breed Consideration: The best-of-breed approach (e.g., pairing Zscaler (SSE) with a third-party SD-WAN like Cisco or Versa) offers specialized excellence in each component. However, the integration burden, policy synchronization, and finger-pointing between vendors during troubleshooting often outweigh the technical benefits for a mid-sized company.
For multi-region deployment, a vendor with a proprietary Global Private Backbone (like Cato) can offer predictable performance superior to relying solely on the public internet, which is a major advantage for reducing latency across continents.
Real-World Application and Best Practices
Thought leadership in SASE is grounded in practical application. The shift to SASE is not just about technology; it’s about transforming IT operations from a reactive, hardware-centric model to a proactive, cloud-centric service model.
Case Study Spotlight: Global Agility Through SASE
Consider the case of a global enterprise, such as Swissport, the world’s largest ground-handling company, which operates across 279 airports in 45 countries [4]. While larger than a 300-seat company, their challenges mirror the multi-region mid-market: a mix of legacy networks, inconsistent security, and a desperate need for centralized visibility.
- The Problem: Swissport relied on a patchwork of MPLS and regional SD-WAN solutions, leading to performance variability and a lack of centralized visibility. Expanding to new locations was slow and resource-intensive.
- The SASE Solution: By adopting a converged SASE platform, Swissport connected over 320 sites and cloud instances to a single cloud-native service.
- The Outcome: The IT team achieved a single pane of glass for network and security management. New site deployment was reduced to “just a few clicks,” dramatically increasing business agility. Furthermore, the centralized visibility allowed the IT team to identify and resolve a performance issue in a South African location in just 15 minutes—a task that would have taken days under the old architecture [4]. This demonstrates the power of a unified, cloud-native approach to deliver rapid ROI through operational efficiency.
Best Practices for Policy Governance and ROI
To maximize the return on your SASE investment, focus on these best practices:
- Prioritize User Experience (UX): A secure network that users bypass due to poor performance is not secure at all. Use Digital Experience Monitoring (DEM) tools within your SASE platform to continuously track user-to-application latency. A good SASE platform should be “always-on” and non-disruptive, replacing the need for users to manually connect to a VPN.
- Embrace Identity as the New Perimeter: Move beyond IP addresses and port numbers. Your security policy should be based on who the user is, what device they are using, and what application they are trying to access. This is the core of ZTNA and is the most effective way to secure a distributed workforce.
- Leverage AI and Automation: The complexity of managing global security policies is too great for manual processes. Choose a SASE platform that uses AI and machine learning for threat detection, automated policy enforcement, and security orchestration (SOAR) integration. This allows your lean IT team to focus on strategic projects rather than constant firefighting.
- Consolidate and Decommission: The true ROI of SASE comes from eliminating redundant security appliances (firewalls, web gateways, VPN concentrators) and networking contracts (MPLS). Aggressively decommission legacy hardware and services as you migrate to the cloud-delivered SASE model.
Conclusion: Securing the Future of the Distributed Enterprise
For the 300-seat, multi-region company, SASE is the inevitable evolution of IT infrastructure. It transforms a complex, costly, and vulnerable patchwork of regional networks and security tools into a single, agile, and high-performing cloud service. By following this six-phase playbook—from meticulous discovery and architectural decision to phased migration and continuous optimization—IT leaders can successfully navigate the transition. The result is a network that not only secures the enterprise with Zero Trust principles but also acts as a catalyst for global business agility and growth.
Frequently Asked Questions (FAQ)
Q: What is the main difference between SASE and SD-WAN?
A: SD-WAN (Software-Defined Wide Area Network) is primarily a networking technology focused on optimizing connectivity and routing traffic. SASE is a framework that converges SD-WAN capabilities with a comprehensive suite of cloud-delivered security services (like FWaaS, SWG, ZTNA, and CASB). While SD-WAN is a component of SASE, SASE provides the unified security and global policy enforcement that SD-WAN alone lacks.
Q: Is SASE too expensive for a 300-seat company?
A: No. While the initial investment may seem significant, SASE often provides a superior TCO compared to maintaining a “best-of-breed” stack of separate networking and security appliances. The cost savings come from:
- Eliminating capital expenditure on hardware (firewalls, VPN concentrators).
- Reducing operational costs (less maintenance, fewer support contracts).
- Improving IT efficiency (single management console).
Many vendors offer tiered licensing models that are highly competitive for the mid-market.
Q: How does SASE handle my on-premises data center applications?
A: SASE platforms use lightweight connectors or edge devices deployed in your data center or cloud environment. These connectors establish secure, outbound-only tunnels to the SASE cloud. This allows remote users to access internal applications via Zero Trust Network Access (ZTNA) without ever exposing your data center to the public internet, effectively replacing the traditional VPN.
Q: How long does a full SASE migration take for a multi-region company?
A: For a 300-seat, multi-region company, a full migration typically takes 6 to 12 months. The longest phases are the initial discovery/planning (Phase 1) and the phased global rollout (Phase 5). The key to speed is choosing a single-vendor solution with a mature global backbone, which simplifies integration and reduces the time spent on troubleshooting.
Visual 1: SASE Vendor Comparison Table (300-Seat Focus)
- Type: Table/Infographic
- Content: The table presented in the “Review of Key SASE Vendors for the Mid-Market” section.
- Purpose: To provide a quick, comparative view of the four major SASE vendors based on criteria relevant to the mid-market (Architecture, Simplicity, Cost, Key Strength).
Visual 2: The SASE Convergence Diagram
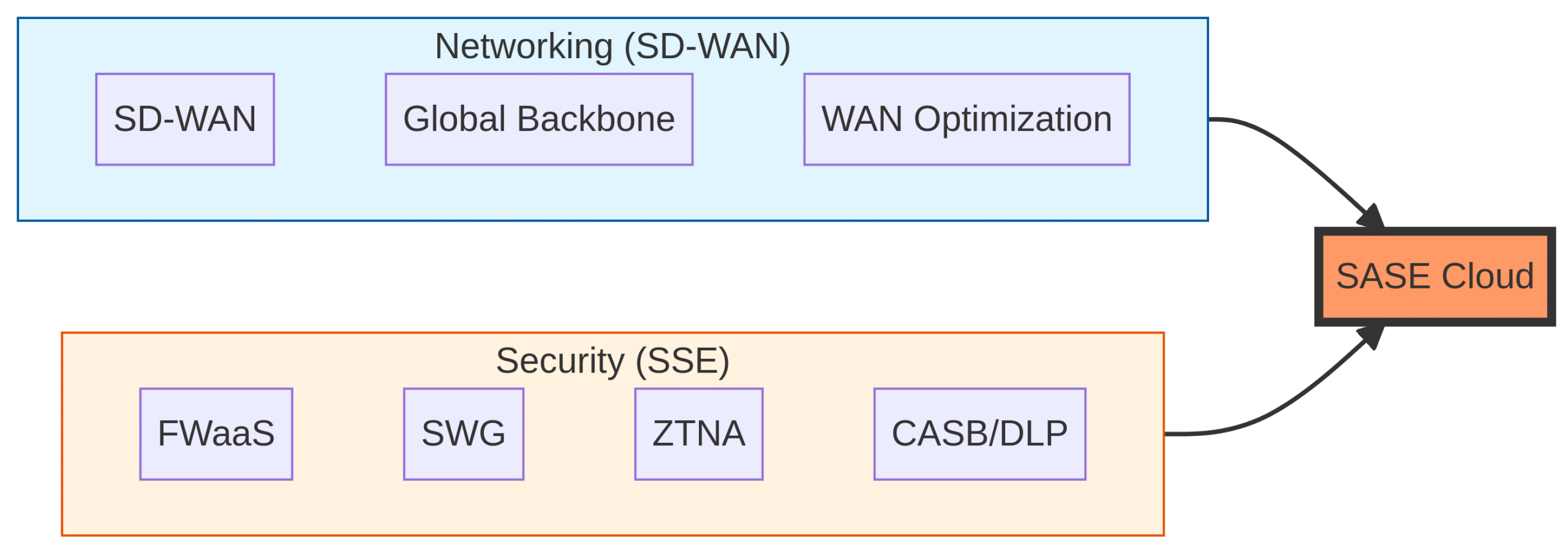
Figure 1: SASE as the convergence of networking and security services.
Visual 3: The 6-Phase Implementation Lifecycle
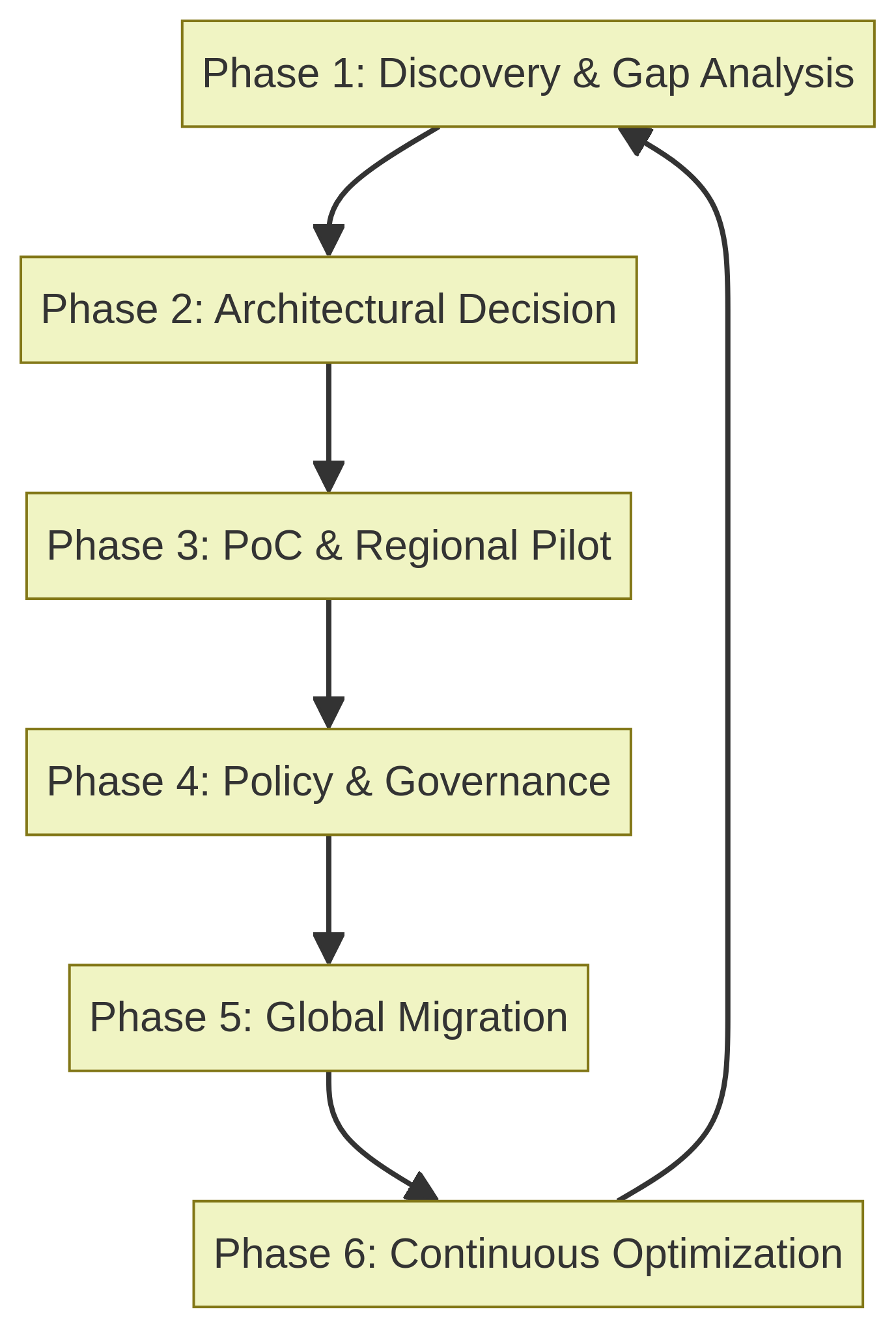
Figure 2: The six-phase roadmap for successful SASE implementation.